The Best Cryptocurrency Wallets – Guide and Reviews
01.Starting Guide:
What is a Cryptocurrency Wallet and Why do I Need One?
For the purpose of using crypto coins, you need to have your own wallet. Differently, to the pocket wallet, you’re not actually keeping your assets inside. Cryptocurrencies and all the transactions related to them are stored in the blockchain. So, basically, the wallet is the key to access your funds.
If you’re interested to know some more about the wallet’s features and what else you can do with it, then jump directly to the dedicated section. Anyway, in order to find the most suitable wallet, you should first think of the coins you want to interact with. Let me invite you to check on my coin list to have a better overview how proceed. Some of you might be interested in how the wallet works to get more aware with the basics – if this is the case just keep reading.
Wallet Access: The Importance of Public & Private Keys
At the moment of initially creating your wallet for the cryptocurrency, you receive a couple of public and private keys to enter the blockchain database. Think of your public key as your bank account number – this is your wallet ID, also called address. Whenever someone would like to send you a number of coins, he’ll need your public key. The private key is another story. Here, we observe a different nature – it’s strongly recommended to keep it safe and only for yourself. Why? Use it as your password to protect your funds. It gives you all the control to sign transactions via cryptographic signature, which is a must-have condition to send it to another user. The one who owns the private key has all the funds in the public one.

A bit worried about your funds’ safety? No need – the consensus method, implemented in the cryptographic process ensures that nobody can fake transactions in the blockchain. There is no room for any manipulations, no central authority to change the rules. Simply the blockchain technology, which makes us all so excited, that we can’t hide it.
Safety hints:
Safety
Threats aren’t just theoretical. The digital nature of crypto is open for scams on a daily basis. What is more, wallets are the entry point to your wealth, which makes them a target group for hackers. Here’s the time to feel responsible for everything you might want to do. There’s no institution to protect you, respectively no restrictions to rely on. It’s the freedom to send or receive funds, which comes with the heed to preserve them.
Key
Losing your private key, means completely dropping control of the assets in your wallet. If you’re not some kind of a mnemonist who’s able to memorize a 40-digit alphanumeric public address and 64 symbols of a private key, then you’re completely done with ever accessing your coins. Having your credentials – you and only you might be a bit too much of a load to carry on. If you somehow lose it – there’s no recovery, no support and no way back.
Backup
For the sake of avoiding such cases, you should always backup your wallet. You know what? Even when I backup, I print multiple copies of my pass phrase and password and hide them in different locations. I really don’t like the idea that someone may have unlimited access to my funds, so I always do a backup of my backup. This and much more details find in the backup section.
02.The Best Crypto Wallet and How to Find it
There isn’t a universal wallet, matching all kind of user needs. Depending on what you’re planning to do with it, there are different types of crypto wallets to satisfy your expectations. First and foremost is the question “What coin you want to use?” because wallets are compatible to a limited number of blockchains only, sometimes they are compatible to only one coin. If you know the answer to that question, click in the following table the coin/token you are interested in and you can read crypto wallet reviews that would make your choice easier.
Popular Coins and Their Matching Wallets
There is an alternative Option to find the best cryptocurrency wallet for you. You can also first think about the wallet type you most likely want to use, which means how you want to handle your coins. After that decision there is still the question what coin(s) you want to use but we will present you already a nice option suitable for most of the important coins.
Wallets by Type |
||||
| Type | Use Case | Top Performer | Essentials | Get Wallet |
|---|---|---|---|---|
| Desktop Wallets |
A software to install on your PC to access your assets |
Exodus Full Review |
Hierarchical Deterministic ShapeShift Single-Factor Authentication |
Download |
| Hardware Wallets |
Offline device keeping your keys with whom you access your coins |
Ledger Nano S Full Review |
Hierarchal Deterministic Two-Factor Authentication Paid Usage |
See Pricing |
| Web Wallets |
A cloud service, which is reachable via any browser |
Blockchain Full Review |
Two-Factor Authentication Hierarchal Deterministic Lack of Key Ownership |
Register |
| Mobile Wallets |
A mobile application serving you as an access point |
Jaxx Full Review |
Multi-Platform ShapeShift Single-Factor Authentication |
Download |
03.What You Can Do With a Wallet
Here, I would like to start with a short summary on everything you’re about to read in this section, for the purpose of feel completely free to jump directly to what interests you most. Check it out:
How to Use a Cryptocurrency Wallet?

Something’s missing? Let me guess, you’re probably thinking of the so-called mining? Well, in order to mine, you’re not supposed to have a special kind of a wallet, but simply one to keep your mined coins it.
Check Your Balance, Send and Receive Funds
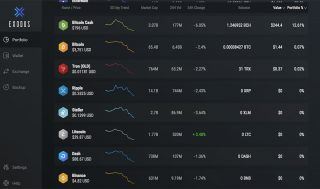
As you might suggest, these are the basic functionalities a cryptocurrency wallet should give you the opportunity to use. Checking your balance is an easy to perform action, which requires you to simply start the wallet and login. Starting up sometimes might be via browser, software or app, depending on the wallet type. And logging is related with entering either a password or a pin. It all comes to the security features and level. If that is what you are mostly interested in, jump directly to the Security section. Back to balances, when you start your wallet, usually you’re about to see your balance. If it’s a multi-coin supporting one, there will be a portfolio with all your assets and their amounts in your possession.
Receiving funds is nothing but sharing your public key for the sake of receiving some coins into your wallet address. Simply copy and paste it to the person who’s going to send you a transaction to avoid any mistakes by typing it manually. Doesn’t matter the channel you choose, you can do it via email, social accounts or even a written letter. Instead of sharing it, you can also create a QR-code to scan with a smartphone’s camera, in case the wallet supports this feature.
Sending isn’t much harder when compared to receiving. Type in the amount of coins you would like to send in the supported currency – either a coin or national one (USD/EUR), enter the recipient’s address and hit the ‘Send’ button. There’s only one element of this process worth discussing it and that’s the fee control, which gives you the option to adjust fees.
Create a New Wallet Address
For the very first usage, you’ll need to create a wallet address. This a complex and complicate to perform process, which is slightly facilitated to clicking a single button “create address”. The software will generate you a random couple of public and private key, based on the cryptographic algorithm, used in the blockchain. Once you do this, you’re ready to receive funds by sharing your public address with the person who’ll send assets to you. In the moment you receive your first transaction, it will appear directly into the blockchain, doesn’t matter that your address is newly created. Here the place to mention that right after you create your wallet, you should definitely back it up, check the following section to understand why. Nevertheless, there’s another option. Some wallets directly create you an address with the initial set up, so there’s no need to additionally do so. Check the review of the cryptocurrency wallet you have choose to adopt the step-by-step guide on how to use it.

Backup and Restore Your Wallet
As already mentioned, if you lose your keys you can no longer access your wallet. So, before you put some coins in it, don’t forget to back it up.
Usually, there’s a built-in back up option in each wallet, which requires you to simply click the button and save a file. Some of the wallets offer the opportunity to back up once your funds, including all the different coins in it, others – don’t.
Of course, there’s also another option, which you might consider. It’s based on your pass phrase (generated from the seed) which is strongly related to your private key.
Back up and restore via .dat file
Once you extract the backup file, keep it in a safe location. When the restoring time comes, replace the .dat file with the backed up one. Consider that your wallet should be empty when performing this procedure, otherwise your funds will get lost.
Back up and restore via pass phrase
When the seed is generated save it well. When you decide to restore your crypto wallet, you’ll need to enter the words from it.
Fee Control

Each transaction requires some fees to get broadcast. Of course, It’s way lower when compared to the bank’s one, but it still depends on the blockchain. If the wallet supports this functionality, you can set your own fees. What you need to know here is that miners are choosing transactions to put in the next block. How do they make their choice? It’s pretty simple – they pick the transactions with higher fees to include in the next block, so the ones with lower fees are somehow in a pending mode. This happens because fees are the miner’s reward, so if your transaction is truly important, you should consider setting a bit higher fees to ensure it will get its place in the next block. However, if you want a faster performance, you can raise it even more for the purpose of get included as early as possible. I suggest you adjust fees only in case you’re enough familiar with the thematic and understand how the blockchain technology works. Otherwise you might experience some issues from avoiding the automatically suggested fee. This dynamic model is regulating the balance between the number of transactions loaded in the blockchain and the estimated time to successfully broadcast them to the public ledger. A good example of fee controlling wallet is MyEtherWallet.
Create QR-codes for Sharing Your Wallet Address

In order to facilitate each transaction, wallets often offer the option to export your wallet address in the format of a QR-code. This is a small graphic image, created from black and white pixels, which you can print and show to someone. The sender has to scan it with a mobile device, and this automatically gives him your wallet ID, where he can send you a certain amount of coins. This is considered as an easy and convenient solution for people, using mobile wallet apps.
Staking for Passive Income
I won’t sugarcoat the truth – this is an option for more experienced users. The idea behind is to aim for a passive income, while supporting the network. You’re supposed to keep your cryptocurrency wallet online 24/7 and lock an amount of coins for the purview of staking. For being part of the network, you’re going to be rewarded. How do you participate exactly in the process? Well, you’re verifying blockchain transactions without scamming or trying to manipulate the network, because otherwise you’ll lose your funds. So, this isn’t just an investment, but more or less a responsibility you take when becoming a full node.
Anyway, this option is available only when speaking of coins, based on the Proof-of-Stake consensus mechanism (this is totally different from the Proof-of-Work, also knows for mining purposes). Some of the most profitable project to consider for staking purposes are PivX and Particl. The number of coins you’ll have to lock in your wallet is usually a substantial investment and the interest rate is realistically around 1%. How to proceed in this case scenario? Download and sync your wallet and unlock your coins for staking. Just keep in mind you’ll need to store the blockchain’s size on your PC and this might mean hundreds of gigabytes. As already mentioned, staking’s initial idea is to support the network by becoming a full node but think of it also as an investment to try your luck on. Check some more interesting details on the website Staking.com.
Exchange Coins – Within a Wallet or a Trading Website
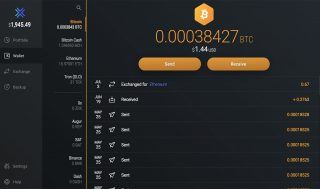
In multi-currency wallets, you frequently have a built-in exchange feature to easy switch funds from one coin to another. For example, if you hold 10 bitcoins and you decide to change one of them into ethers. You have to simply click the exchange function in your wallet, pick the coins types and the amount you would like to swap. Some of these implemented features support en equivalent of the amount in a national currency (USD/EUR). A good example is Exodus, with its feature called ShapeShift, more on which you can read in the detailed review. Just have in mind that this easy to use service might charge you with higher fees. So, if you’re willing to have the best price, you might want to finally use an exchange. There you can also cash out your coins into fiat currency or buy some other assets.
Act as a Full Node to Support the p2p Blockchain Network
Supporting the blockchain network is usually a principle, reincarnated in a coin’s official wallet. I personally consider it a passive action from the user’s side, but it might be extremely important for the project you’re connected to. It all comes to downloading the whole blockchain to serve as a full node. This way you’re becoming part of the peer-to-peer network by validating transactions and working in cooperation with other nodes.
As soon as you run your wallet, the process will start automatically when you sync the blockchain with your device. Once again, note that the blockchain’s size might be huge, depending on the coin, so there will be a constant traffic at your internet connection. This is the reason why most of the multi-coin wallet are working as light nodes, otherwise it might take forever to sync with all the coin’s blockchains.
04.Overview and Comparison of the Different Types of Wallets
As I reviewed in the guide section, a cryptocurrency wallet is just your access to connect your funds, which are stored in the blockchain. You can use your couple of public and private key via different devices – from your desktop, your handy or a third-party service website. In this section, I would like to explore the different types of wallets and give you some hints on all their strengths and weaknesses in the diversity of their usages.
| Type | Pros | Cons |
|---|---|---|
| Desktop |
Pros Ensure privacy, easy access and TOR anonymity |
Cons Susceptible to hacking attempts |
| Mobile |
Pros Practical and simple, suitable for trading |
Cons Can suffer viruses, keyloggers and malware attacks |
| Web |
Pros User-friendly for sending and receiving |
Cons Private keys are saved on a third-party server |
| Hardware |
Pros Most secure for long term holding and saving |
Cons Need batteries and cost money |
| Paper |
Pros Best for saving and more secure than the others |
Cons Can get damaged with time or stolen |
Desktop Wallet
As you might imagine, this is a wallet, you’re installing on your desktop, usually in a Windows edition, but most of the wallets already offer downloads for other operation systems, such as Linux and MacOS. This is the most commonly offered wallet type, because each project wants to propose the option to their users to become a full node and support their network. This happens by downloading the software and taking up a lot of hard disk space. This is the reason why users frequently use a third-party service – to avoid the blockchain size issue. An excellent for a desktop wallet is the most popular in 2018 Jaxx wallet. I want to mention also the opportunity to use a browser extension when it comes to Chrome and Firefox.
Mobile Wallet
Looking for simplicity and ease of use? You’re always on the go and need a wallet to follow you anywhere at any time? You’re definitely looking for a mobile one. Download it from your app store in either Android or iOS version. Just keep in mind that not all the wallets are compatible to both operating systems, so check twice before you download whatever. If the wallet doesn’t support it, but there’s an option to download it anyway – it might be a scam. Want a wallet name to search for? You should definitely consider Coinomi.
Web Wallet
Sounds familiar to you? Yes, this is simply a website – an internet service to hold and manage your coins with. An easy to use and access wallet from any kind of device, which is connected to the internet. Unfortunately, you rarely possess control over your private key. That’s why it’s considered a vulnerable to hack attacks type, where you need to count on the integrated security measures and nothing else. An example? I suggest for sure the Guarda one.
Crypto Exchanges
When you use a crypto exchange, it automatically provides you a wallet address for respective reasons. There’s no way to operate with coins without it and perform actions such as buying, selling or trading. You don’t have a full control over your private keys here and this is what makes exchanges a prime target for hack attempts. It’s safe to transfer and exchange coins, but I don’t propose it as an option to store large amount in it. Let me point you out some of the most trusted and reliable exchanges with lots of currencies supported:
Best Exchanges for 2025 |
||||
| Exchange name | Deposit methods | Supported assets | Essentials | Try it |
|---|---|---|---|---|
| Binance Full Review | Cryptocurrencies | BTC, XRP, ETH, NEO + 150 more |
Large number supported assets No fiat deposits |
REGISTER NOW |
| BitFinex Full Review | Fiat bank transfer | BTC, BCH, LTC, EOS + 35 more |
Very advanced platform High trading requirements |
REGISTER NOW |
| CoinBase Pro Full Review | Fiat bank transfer and CC | BTC, ETH, ZRX, LTC + 2 more |
Credit card deposit Few tradeable coins |
REGISTER NOW |
Paper Wallet
Here, you’re not able to manage your coins, but just keep them offline and safe. You’re basically printing out a piece of paper with your public and private key (as a string or a QR-code). The thing is that you should keep this one extremely secured and make multiple copies. They in turn should be stored in various locations, as to make sure you’ll always have at least one safe, no matter what.
Brain Wallet
This isn’t really a wallet to do something with, but more or less a highly secured idea on how to keep safe your funds. I’m talking of memorizing your seed phrase without recording it anywhere. Literally keep it your mind using different memory techniques. I don’t recommend you try this one, because of something happens with you – maybe forget it or become permanently incapacitated, your funds will be lost forever.
Other Important Factors to Differentiate Wallets
In this section, I would like to show you some classifications when it’s up to wallets and what are the basic difference in their technical concepts. Let me first sum it up for you:

Single/Official vs Multi-Coin/Third-Party Wallets
We’re witnesses of many interesting crypto projects out there born every single day. It’s totally normal that some of you might want to support and use more than one, so here it comes the purpose of the multi-coin wallets. Third-party providers offer the opportunity to have larger portfolio of services for users who doesn’t want to stick with a single coin. Official wallets are single coin ones, which are supporting the particular project’s asset on the current blockchain platform. Despite this restriction, these wallets are still in usage, regarding the development of the coin and the opportunities to support its network. In fact, there you can profit one of the most advanced function when handling your coins. Ultimately, have a look at the coin list, where you’ll find a link to overview a coin’s wallet options and also the multi-coin wallet supporting your asset. In breve, this option is perfectly described in the Jaxx wallet review – one of the most popular wallets nowadays.
Cold vs Hot Wallets
I consider this classification as one of the most frequently used, so you’ll need to really understand the difference between these two. When you read ‘hot’ wallet, you’re supposed to think of internet connection. This is a whole the time online wallet, which makes it vulnerable and likely to get compromised. This is because a hacker can easily get access to your device and steal your keys. To prevent it, you should increase your security level, which highly depends on the overall measures of your operation system.
When people say cold wallet, you should imagine an offline for most of the time connection. Keys here are stored in a manner which is way harder to access them. You have to bring your device online only for short periods of time, for example when broadcasting a transaction. A popular representative, you might be familiar with is the hardware wallet, which requires you to approve a transaction using the device’s button (no hacking attempts possible). If you want a name to read some more about, I strongly recommend you Ledger. It’s not like It’s much more different when compared to Trezor, but it’s adapting features faster and aims for an innovative nature. Want an example – check the cooperation between Ledger and Particl. Just for the record – Trezor is still in negotiations with Particl.
Full Nodes vs Light Nodes
Every device connected to the peer-to-peer network is considered a node. There’s a difference between the different types of nodes, their functions and purposes, so it would be good to clear it now. A full node is verifying the consensus rules and that’s why it contains all the blockchain information.
| Node Type | MIN Free HDD | Transactions Check | Sync Time | Support Network |
|---|---|---|---|---|
| Full | Yes |
Yes |
Slow |
Yes |
| Light | No |
No |
Fast |
No |
A light node on the other hand don’t download the blockchain locally but connect to full nodes when need any information. This is very useful for third-party desktop wallets and also mobiles, because of the lower disk space requirements.
Deterministic vs Non-Deterministic Wallets
The distinguishing here is based on how the cryptocurrency wallet is initially created (regarding its keys). If the couple of public and private address is randomly generated, it’s called a non-deterministic wallet. On the other hand, if it’s based on a seed, which is reproduceable, then it’s considered deterministic. If you’re in a situation to recover and restore a deterministic one, then you simply use the seed. For the non-deterministic, you use the back up before restore option. What about their usage? Well, deterministic are for example the hardware wallets. If you carefully store the seed, even if you lose the device, you’ll be able to save your funds.
Custodial vs Non-Custodial Wallets
The classification here is concerning the way a pair is handled – your full control or a third-party intervention. When speaking of custodial wallets, someone else is in charge to care about your private key – you rely on the service and use the security they provide you. Non-custodial (hosted) wallets give you full control over your private key, respectively you’re responsible to keep it safe. Situating the theory in practice, I observe that web wallets and crypto exchanges are mostly custodial representatives. Nevertheless, desktop and mobiles can also be custodial.
05.Basic Security Measures You Should Know
You don’t need to be a security expert to keep you funds safe. There are several easy to follow rules and security options you might consider using. I’m going to stop by to the most important security features, as well as some general advices on how to proceed if security is your most important criteria to choose the best cryptocurrency wallet for yourself.
General Security of Your Device
Security isn’t always up to the wallet, but it also depends on the system, running your device. There’re frequently experience issues such as malwares, viruses and trojans, which can catch keystrokes and screen captures to find out keywords. Such programs can even change the transactions you send to the network by changing the recipient’s address. That’s why, I recommend you ensure your firewall (keep it always up-to-date), put some virus protecting software and everything else applicable to your operation system. Another hint I would like to reveal you is to always check the website’s domain field: it should begin with HTTPS, rather than HTTP and the padlock sign next the URL should always be in green. Never open any suspicious or unknown links, sites, apps or whatever and this way you’ll avoid any general security issues.
Password Protection and Encryption of Keys
For the purpose of securing hot wallets, keys are often stored in your crypto wallet in encrypted form, which can be accessed only with a password, which opens the software. So, always choose a strong password, but also keep your system safe nonetheless, because any keylogger can catch and transmit your password to a hacker. Most of the wallet types usually use a password to restrict the access to it.
Two-Factor Authentication
This is an additional security layer, which requires a second confirmation before a transaction gets broadcasted to the network. If a hacker enters your wallet and aims to steal your funds, he would need an additional information to do so. You can put for example an email or SMS confirmation to request you each time you send some coins. This way you’ll be always aware of what’s happening and might try to prevent it. An example of wallet with a 2FA is Coinbase.
Multisignature
This is considered a security feature, because it requires several people to confirm a transaction before it gets send. This is usually used by shared or company accounts, but you can also do it for the sake of securing you assets. Electrum is a good example of a wallet that has implemented this feature. Visit the in-depth review to learn more about its additional privacy and anonymity functions.
How to Safely Store Your Backups
Even if I already cleared the importance of the backup as a process itself, I would like to one more insist on how important is it to keep your back up copy safe. Start with making sure you have it on multiple places and ideally go offline to rule out any possibilities to get hacked from using different data storages. You can save this in a USB drive, SD card or even a paper wallet, just keep the storing device offline. And again – not only putting it to different devices, but keep it in different places, such as bank vaults.
Finally, it’s all up to the amount you’re planning to store. If you have ten dollars inside your device, it’s probably not worth it to hire a deposit box to keep it safe. But if speaking for a hundred thousand, you might think in another way, don’t you? Ultimately, don’t put on crypto more than you’re ready to lose.
In a word for paper wallets, either if you choose a tool or simple download option, in both cases you’re using a browser to proceed. So, make sure you’re out of the internet connection when typing your private key. And remember, even if it looks trustworthy, even a single package send is enough to give away your savings.
- In case of using a web service, close the browser after you’re done and check if no cookies for this website were saved (if yes – delete it).
- In case of download tool, after you close it stop all the background tasks running before you get online again.
06.FAQ
-
What happens with two users receive the same keys?
Creating the same public key by chance would means the same private one too. This is mathematically unlikely event, but it’s not completely impossible. As an example, let’s take an address with 32 characters – a Bitcoin address ranges from 26 to 34 bytes and Ethereum’s ones are around 40 chars. One byte has 8 bits, 32 bytes are 256 bits, which means there are 2^256 possible combinations. This is insanely huge number with around 77 digits – roughly the estimated number of nucleons of the whole observable universe. Therefore, you don’t need to worry about this. -
What happens if I lose my passphrase?
Unfortunately, if you lose your passphrase your funds are most probably lost. Some wallets provide multiple recovery options of your password via pass phrase but if you lose the last-mentioned, you should most likely consider creating another wallet. -
Why I would like to change the wallet’s fee?
The higher fee you place, the faster your transaction will get broadcasted. The reason behind is that miners receive it for their contribution in the network (validating and adding transactions). If you put a higher fee, your transaction is most likely to be added in the next block.